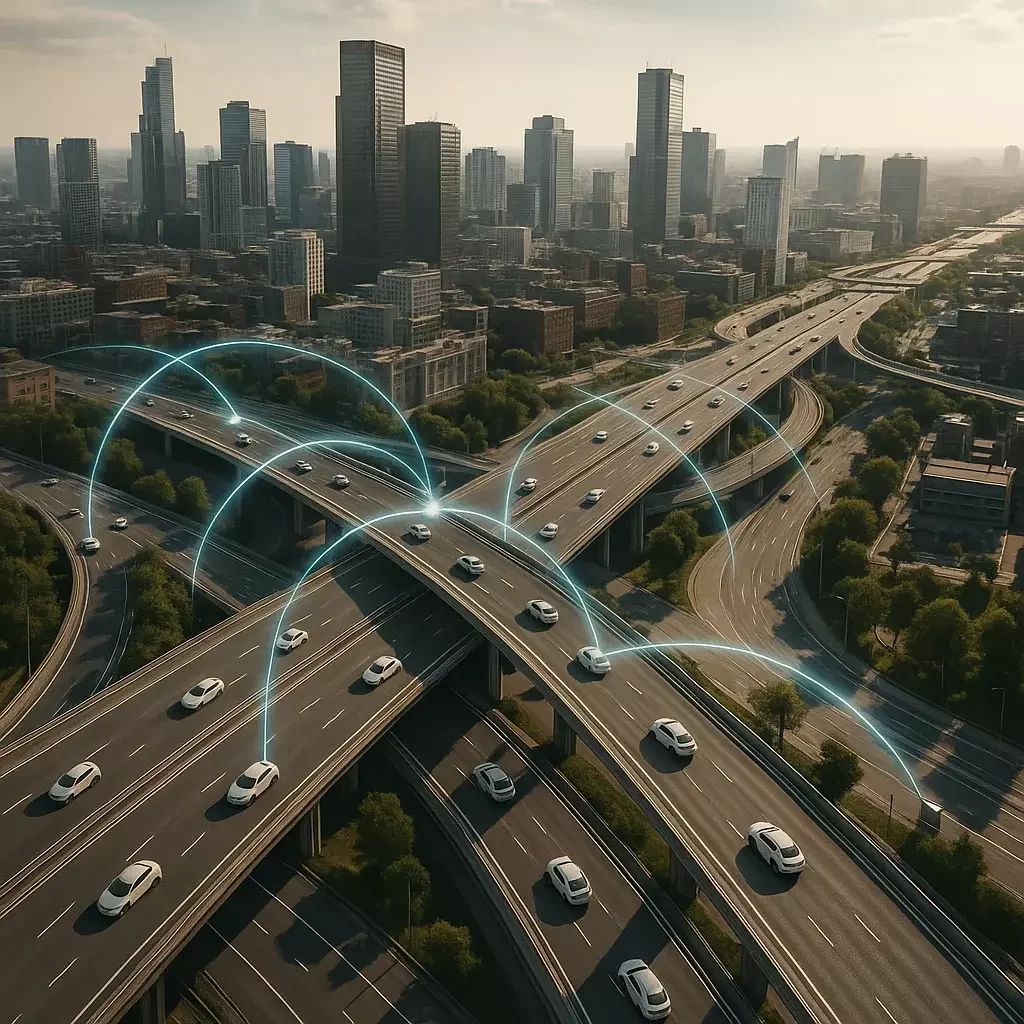
The Problem:
Current Infrastructure Cannot Support Safety-Critical Operations
Our team excels in delivering impactful strategies with measurable results. From brand visibility to market recognition, we bring expertise and innovation.
Vulnerability
Current 5G networks lack the resilience required for safety-critical resilient operations in dynamic and hostile environments. When seconds matter, standard commercial architectures fail to deliver necessary redundancy and security protocols.
Fragmentation
Complex industry and business operations cross domains, jurisdictions, and spectrum bands, creating integration nightmares. Legacy systems force operators to manage multiple disconnected networks.
Latency
Autonomous systems require ultra-reliable low-latency communications (URLLC). Current networks introduce unacceptable delays for high-speed, dynamic platforms operating in three-dimensional space.
What we do at DigitBeez
Crafting ideas that inspire
At DigitBeez, we believe in transforming creative ideas into meaningful digital experiences. Our team works tirelessly to deliver impactful solutions, ensuring that each concept reaches its full potential for businesses and individuals alike.


Our outstanding achievements
Explore our portfolio to see the innovative projects we've completed. Our work reflects creativity and strategy, delivering impactful results that drive success for our clients across various industries.
1000+
Customers
60+
Products
30+
Awards
Creative showcase
Our portfolio
Purpose-built for adversarial, harsh, and safety-critical environments; the platform is the first to incorporate standards-driven AI/ML intelligence across the stack with resilience against cyber and physical threats.
01. Adaptive Security & Policy Control
Adaptive Security &
Policy Control
A suite of distributed AI privacy-preserving security analytics offering early detection and rapid mitigation of threats, enabling network functions to autonomously and safely adapt their policies and behaviour in response to evolving conditions, with rigorous guarantees.
Formal verification embedded into the control-plane learning uses a probabilistic model validator and constraint enforcement so that the AI agents never violate safety-critical invariants with adaptive algorithms proving they won’t break determinism or service level agreements as they learn – a key differentiator from unbounded RL approaches.
A lightweight adaptation layer quickly fine-tunes the policy to local conditions with minimal data, achieving sub-10 ms re-convergence allowing truly self-driving networks that learn and adapt in real time without lengthy retraining – a breakthrough for handling 6G’s variability.
Real-time & autonomous security policy and operational parameter adaptation to dynamic threats, while guaranteeing safety-critical performance and resilience in hostile and failing environments.
02. Unified Policy Enforcement
Unified Policy Enforcement
A secure, low-latency bypass path that implements mitigations without disrupting normal traffic and signed with quantum-resistant cryptography to protect against future quantum attacks on network control channels. The network to evolves defense posture autonomously - guaranteeing stability and safety at every step and preventing any violations of core reliability constraints.
Neuromodulated prioritisation focuses resources where it matters most; ensuring that even under resource strain, the most dangerous threats are addressed first. The result is a 6G network that is self-healing, self-optimising, and provably trustworthy.
03. Autonomous Trust & Consensus Platform
Autonomous Trust & Consensus Platform
Delivers continuous safety-critical network functions and services under adversarial conditions by hardening and securing the control and data planes against faults and attacks - enabling the network to optimise fault tolerance and performance on the fly.
Makes consensus and network control robust against node compromises and transient faults by autonomously tuning fault tolerance levels and sharing learned policies across the network in real-time. Even during coordinated attacks, compromised networks functions and services are isolated in milliseconds, preventing cascading failures across the network.
04. Intelligent Threat Detection & Analytics
Intelligent Threat Detection & Analytics
A suite of distributed AI privacy-preserving security analytics offering early detection and rapid mitigation of threats with network functions autonomously and safely adapting policies and behaviour in response to evolving conditions with rigorous performance guarantees.
The proactive defense layer adapts as fast as the threats do using Distributed Federated learning at the edge ensuring no single point of failure or data leak in the analytics system. Graph-based threat modeling catches complex multi-vector attacks that siloed security tools overlook. Together, these innovations identify and neutralise emerging threats before they escalate.
05. Mobility Intelligence Engine
Mobility Intelligence Engine
AI-Driven Mobility Management: Leveraging on-device, RAN, core, and OAM/management AI for seamless cross-domain mobility, predictive resource allocation, anomaly detection, and dynamic path optimization. This allows uninterrupted service for fast-moving fleets, UAVs, or tactical teams. - Secure Multi-Domain Integration: Built-in interoperability between terrestrial 6G, maritime networks, aerospace platforms, and satellite constellations. Enables uninterrupted communications across land, sea, air, and space. - Low-Altitude Economy Enablement: Optimized for new mobility economies, including UAV fleets, high-speed rail, maritime drones, autonomous convoys, and emergency response.
Meet our team of experts
Our talented and diverse team is dedicated to delivering innovative solutions, ensuring your brand stands out in today’s competitive digital landscape.

Sigrid Rogers
Creative Director
Sarah Patel
Digital Marketing Strategist
Michael Dawson
Lead Developer

Arokia Reed
SEO Specialist
Investor Relations
Sign In or Sign Up to the Investor Relations site if you are an Institutional or Qualified investor. We onboard you within 24 hrs.
Come meet us today!
Our Offices
Visit us any time for in-person consultations and project discussions.